You will see the status of your hard disk after a short delay. Reboot your PC, and after it’s switched off and on again repeatedly, pressing Delete, F2, F12, or whichever button the boot screen tells you, will take you to your BIOS. You can also set Windows 10 to boot directly into the BIOS. Even if you don’t see any errors on your computer, it’s best to scan it periodically.
- This application failed to start because .dll was not found.
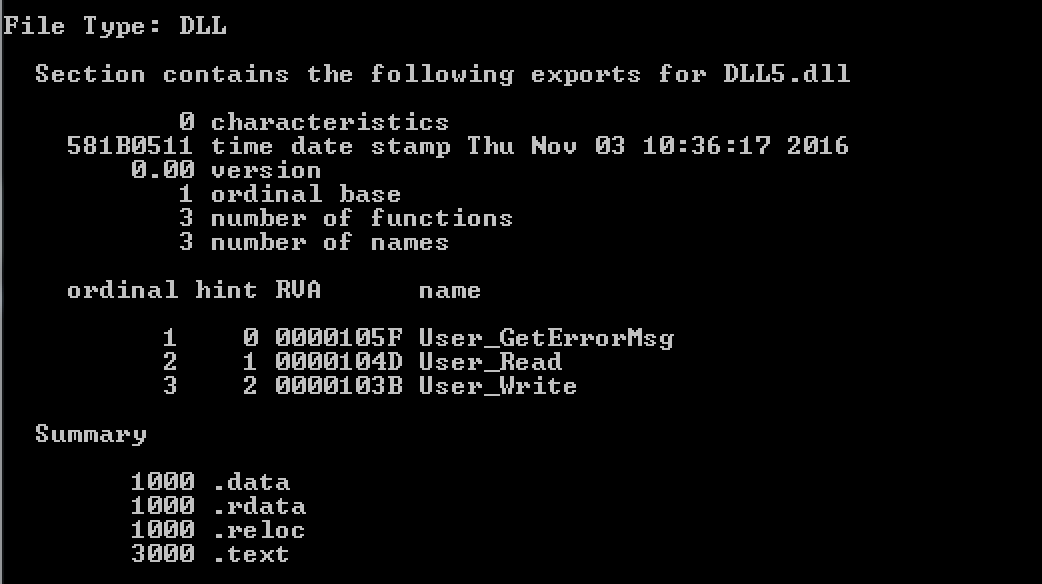
- 1.EXE is an extension used for executable files while DLL is the extension for a dynamic link library.
One of the main reasons why this executable is so big is because of the obsfucation method the developer uses. Instead of implementing a single string decryption function, they used one decrypting for loop for each encrypted string, which greatly increased the amount of raw code. S0142 StreamEx StreamEx obfuscates some commands by using statically programmed fragments of strings when starting a DLL.
Except for AC Unity it also shown up for me with Division1 and 2, AC Odyssee, The Crew 1 and 2, Steep (more I haven’t tested yet but I’m sure others are also affected) under Win7 64Bit. I think the UC Devs screwed something up in the update that neglected Win7 and DX11 users. @makru1337 Ok I’m starting to suspect that this issue is localized to Win7 and likely a limitation of DX11 since that’s the newest version that Win7 limited to. @makru1337 fyi…I’ve tried AC Unity, there I get no error message and multiplayer was working for me without waiting long. @gheu007 Having the exact same issue since the last update a few days ago now i cant use shift f2 to add people for raids or friends ect . At first I thought it may be something with my Dx installation but other games from steam launch perfectly without any issues. This information may be shared broadly to reach all appropriate stakeholders.
Picking Real-World Secrets In Dll Files
Click the arrows to open the next branch of folders until you find what you’re looking for. The registry offers a significant amount of system customization, but you should back up your system before you edit the registry.
- S0387 KeyBoy In one version of KeyBoy, string obfuscation routines were used to hide many of the critical values referenced in the malware.
- Martial Gervaise, deputy cybersecurity director of telecom company Orange, tweeted that the Hive ransomware group was behind the cyberattack, citing screenshots of what appears to be a ransom note.
You can use the inverse to enable a two-step, REGEDIT-free Registry file import. Simply rename the Registry file you want to import with a .REG extension. Then double-click the Registry file to quickly import the contents of the file into your Registry. You can’t back out of the import after you’ve confirmed it exists, so ensure you know what you’re importing before you run the REG file. Test this procedure out on a properly functioning system. If you wish to view a REG file’s contents, right-click the file in File Explorer and choose ‘Edit’. Unless you see the «Edit» button, the REG file is probably in a ZIP archive.
Programs In Dll – Some Thoughts
In the example below, the Windows OS is on drive D. To backup logilda.dll a specific key; follow the same instructions above, but drill down to the key you’re after and export that. After creating value for a path, more paths can be added followed by a blank line, or the editing can be closed. Minor customizations like adding a logo to the control panel and system window can also be done. Our technology is deployed on over ten million endpoints and protects hundreds of enterprise clients worldwide including Fortune 100 organizations and government institutions. The notify subkeys are used to configure event handlers that are to be notified whenever certain events happen, related to SAS. Events are things like logon, logoff, shutdown, lock, etc.
